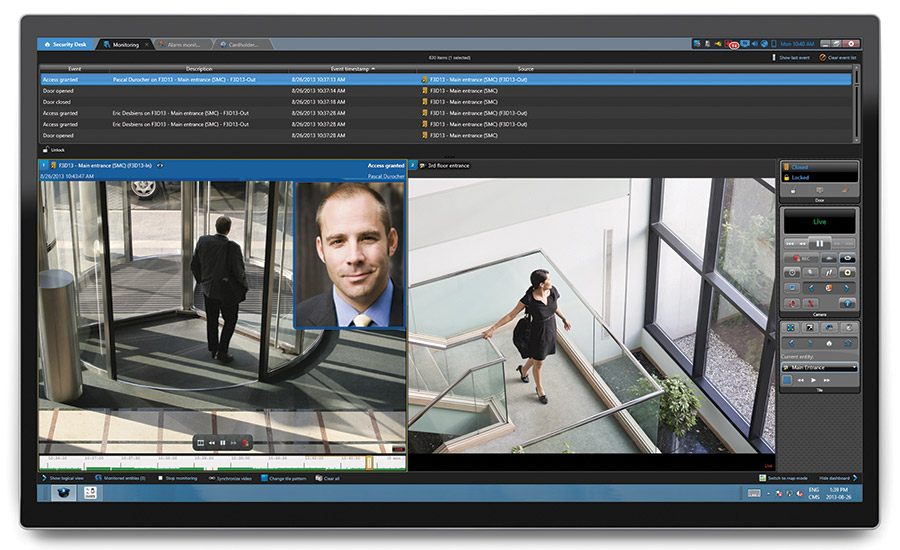
On the Open Path To Merging Access Control With Video Surveillance
Source: SDM Magazine, Jimmy Palatsoukas
It’s an all-too-familiar scene. The security integrator goes on a site visit and observes operators jumping from one monitor to another, navigating through different video surveillance and access control applications to investigate an incident, or more importantly, handle an emergency or threat. This common scenario of security operators trying desperately to piece together information and make objective decisions begs for greater operational efficiency, and becomes the main catalyst for security directors’ ears to perk up when security system unification is brought to the table.
Beyond the ease of navigation and simplified operator workflows and training, there are numerous other benefits to unifying video surveillance and access control systems into a single platform. These include the ability to program alarms, generate reports, conduct maintenance, and streamline upgrades with built-in version compatibility for both video and access control, all from one workstation and interface.
As more projects include system unification within their specifications, it is becoming increasingly important for systems integrators to understand both the operational and technical factors that should be considered, and the pathways that lead to a successful and cost-effective unified installation. Similarly, systems integrators need to keep an eye on the road ahead, as end users gradually veer towards open architecture video and access control systems that provide added layers of flexibility and better investment longevity.
Putting Business Objectives Ahead of System Technicalities
While integrators are sometimes quick to examine the technical aspects of an installation, Paul Boucherle, principal at Matterhorn Consulting LLC, Canfield, Ohio, and Matt Wharton, president, security & technology consulting practice at Guidepost Solutions LLC, New York , N.Y., both recommend taking a step back to focus on business objectives first.
According to Boucherle, who was once selected to spearhead an access control and video surveillance integration at LAX airport, “It’s vitally important to understand how a client is working today versus how they will work in the future.”
More important than that, says Boucherle, is the delivered business value. “If unification of video surveillance and access control streamlined operations, giving each person 10 percent to 15 percent more time, what would the client do with that extra time? Would they focus it on other security processes, programs, or goals for that year? That is one of the least measured returns on investments of unification, but one of the most important for the security directors. It allows them to appeal to senior management by introducing a business case that not only justifies the investment but also shows what the contribution of security is to the organization — and that’s a big deal.”
Wharton, whose team consulted Levi’s Stadium in building out a unified platform using Genetec Security Center and HID Global hardware, adds that an equally essential factor is to understand all the system’s users. “We’re not just looking at the operators of the system,” explains Wharton. “It’s equally important to be cognizant of the level of knowledge and sophistication of the client’s IT department, and get them involved in discussions early on. Furthermore, considering users that are swiping cards, or monitoring more business-oriented applications, ensure you select the right technology that meets all users’ needs.”
Exploring Key Technical Considerations
Once some of the more high-level objectives and considerations have been made, diving into the technical side of things can get somewhat complex. A green-field project is certainly more straightforward, allowing for much more leeway in the design and installation of a unified security system. However, walking into an existing installation where a video and access control system are already installed as separate systems can lead to many challenges.
According to Andy Bowman, founder of SiteSecure, Jacksonville, Fla., a leading security integrator business which was recently acquired by Miller Electric Company, “Having to consider a rip-and-replace scenario is a realistic and common challenge for clients. However, at some point it is not cost effective or reasonable to assume that you can move forward with an existing access control system.
“To put things into perspective and help drive that point, I ask my customers: “How many new installs is brand A, which you currently have, doing in the global access control marketplace? Is anyone still buying this solution? Is the company investing in development or are they holding on to their install base? Simply put, it just doesn’t make any sense to spend hundreds of thousands of dollars to reinvest in a technology that has no forward-moving strategy,” Bowman says.
Vulnerability of an existing access control system should also be scrutinized. In the past, many access control technologies were static, which made systems vulnerable to attack. Yesterday’s access control systems also quickly become anchored to obsolete software, devices, protocols and products, hindering their ability to support and facilitate change. According to John Fenske, vice president of product marketing for identity and access management at HID Global, Austin, Texas, the latest high-frequency contactless smart card solutions exist within a larger identity ecosystem that is significantly more dynamic than legacy technologies such as proximity cards and readers.
Other technical factors that Bowman and his team especially look at are the back-end infrastructure, and the need to possibly upgrade hardware components such as operator workstations, laptops and server platforms to accommodate a unified system. Bowman continues to explain that card and card reader technologies, legacy cabling architecture and circuit boards all need to be closely examined as well, because additional costs may be imposed if these components are not compatible with newer access control devices.
Due to technical limitations of older access control systems, costs can be the most challenging hurdle for some organizations. However, potential return on investment (ROI) can help integrators persuade even the most budget-sensitive customers. According to Fenske, “While it does take an investment to migrate to a new standards-based access control system, this investment comes with a valuable return. An example of a tangible ROI is lower insurance premiums that come from improved risk management. Or, the organization might realize an intangible ROI through improved security that allows them to avoid the costs of a disastrous breach.”
Upgrades Open the Door to Greater Capabilities
In addition to delivering an ROI, today’s access control systems also make it easier to adopt emerging capabilities. For instance, newer solutions enable mobile devices to be used as credentials, which improves convenience, enhances the user experience, and delivers a number of new security opportunities. Mobile access control also simplifies the secure identity management process for facility access, and helps to drive security convergence through solutions that can integrate a multi-layered physical access control system (PACS) and IT security into a single, unified system.
“Cards and phones are already converging into centralized identity management systems,” Fenske explains. “The goal, though, is much more than just supporting both form factors. Even more valuable is the ability for organizations to use cards or phones, or both, to secure access to the door, to their data, and to their cloud applications — all with a seamless user experience. This is possible with converged back-of-house technologies that enable strong authentication and card management capabilities for computer and network logon. These technologies also ensure that physical and logical identities can be managed on a combination of plastic cards, smartphones and other mobile devices, which in the future will also include smart watches, wristbands and other ‘wearables.’”
Many other exciting opportunities are enabled by a move to standards-based access control systems. One of them is gesture technology, which can be used with a phone’s Bluetooth connection to make secure long-range door opening as convenient as simply rotating the device while approaching a mobile-enabled reader. Additionally, moving to a standards-based access control system will make it easier to adopt biometric authentication, which will further improve mobile access security and convenience.
In order to realize these benefits, access control solutions must support the broadest possible range of available handsets as well as legacy ID cards. Support for open standards is critical in order for the access control system to adapt to new requirements and capabilities as the industry quickly moves to a wide variety of new device platforms, biometrics authentication models, and unified cloud-based systems for PACS and IT credential management.
Open Architecture Solutions: Deciding If & Why
Integrators that choose to work with an open architecture access control solution benefit from greater flexibility of integration with various components and devices. Implementing an open architecture access control system also allows their customers to leverage existing hardware to minimize migration costs by supporting a phased upgrade to newer devices.
“The more an integrator can tailor a solution to a customer’s application, the more protection it offers their business. The integrator will know the ins and outs of the system and be in a better position to retain the loyalty of the client. And since it is using non-proprietary hardware, clients can still swap out technologies in the future,” Bowman explains.
Open architecture also provides long-term investment protection, says Boucherle. “With proprietary solutions, if a company starts running low on cash, they quit developing the software. With open architecture solutions, you have many vendors contributing to developing technologies, so it’s a massive advantage. There is more longevity and the solution has longer legs.”
Wharton adds that working with non-proprietary solutions is a strategy that benefits everyone, “Open architecture is ultimately what end users want. Integrators also have an opportunity to promote their reputation and service to establish longer-term relationships that focus on evolving platforms and not necessarily replacing them completely,” he emphasizes.
Customers will always be tasked with increasing the operational efficiency of their security programs. Unification of video, access control and myriad other security modules provides the greatest flexibility, allowing for a cost-effective and pragmatic approach to the evolving security landscape. Leveraging open architecture access control and video surveillance solutions to merge system components will help integrators keep their clients’ best interests top of mind — that is to minimize costs and help protect investments.